|
Friday 9th ,August 2019 You WILL lease MS Office The necessary core functionality of MS Office hasn't changed in 20-25 years. If you've got an older version of Office available, there's little reason to "upgrade" to MS Office 2019, although Microsoft would want you to think so..
There' s just not a compelling argument for paying a recurring fee just for the privilege of using Office.
It is certainly time to start using LibreOffice. Free, fast and hot!
Get yours for free from:

https://www.libreoffice.org/download/download/
-Stu
From ZDNET:
Microsoft removes Office 2019 from its Home Use Program benefits
Microsoft quietly has made a change to its Home Use Program (HUP) for its Software Assurance business customers. As some had expected when the company began revamping the HUP benefit earlier this year, Microsoft is dropping the ability to buy the non-subscription version of Office for a steeply discounted price. Microsoft instead is offering HUP customers the ability to buy Office 365 Home or Personal at a discount for home use.
In an updated Frequently Asked Questions (FAQ) document about the program, Microsoft now notes:
"Microsoft is updating the Home Use Program to offer discounts on the latest and most up to date products such as Office 365, which is always up to date with premium versions of Office apps across all your devices. Office Professional Plus 2019 and Office Home and Business 2019 are no longer available as Home Use Program offers."
Up until this change was made as part of the July product terms, HUP Office benefit allowed Software Assurance customers to buy Office 365 ProPlus (which is the the core set of Office apps for Windows, made available via an Office 365 subscription) or Office Professional Plus 2019/Office Home and Business 2019 (the non-subscription versions of Office for Windows/Mac for small-business users) for a discount. The discounted price for U.S. users was $14.99 for either of these options. The updated HUP for Office option enables business users to purchase Office 365 Home or Office 365 Personal subscriptions at a 30 percent discount. To qualify, customers need to either have Software Assurance or a certain number of Office 365/Microsoft 365 E3 or E5 licences (2,000 for commercial organizations and educational and nonprofit customers). Further down in the FAQ, however, Microsoft notes that those who may already have squeezed in a discounted purchase of Office Pro Plus 2019 or Office 2019 can't get more of those. The FAQ says: "If you have already purchased Office Professional Plus 2019 or Office Home & Business 2019 at a discount through the Home Use Program you will still be eligible for the Office 365 Home Use Program offer."
As the Licensing School UK noted in a recent post, "You can still buy HUP licences for Project and Visio, but licences for the Office products to use at home are now covered by Office 365 Home or Personal subscriptions." Posted by Stu WisePosted : 06:54 AM
post comment
Thursday 7th ,February 2019 Microsoft really doesn’t want you to buy Office 2019 I recommend begining to use LIBRE Office, a fully functional, drop-in replacement for Microsoft Office. Also...IT IS FREE!
https://www.libreoffice.org/download/download/
Microsoft wants you to pay monthly to use Office 365 instead of the one-time cost of Office 2019!
-Stu
Microsoft really doesn’t want you to buy Office 2019
Microsoft today launched a marketing campaign pitting Office 2019 and Office 365 against each other. The goal? To prove Office 2019 isn’t worth buying — you and your company should go with Office 365 instead.
In a series of three videos, twins Jeremy and Nathan calculate the differences in Excel, Cynni and Tanny present their findings in PowerPoint, while Scott and Sean type it out in Word. The ads are cringe-worthy, to say the least, but they do get the point across.
When Microsoft announced Office 2019 in September 2017, the company said the productivity suite was “for customers who aren’t yet ready for the cloud.” And when Microsoft launched Office 2019 in September 2018, the company promised it wouldn’t be the last: “We’re committed to another on-premises release in the future.”
And yet, Microsoft would much rather you join the ranks of Office 365’s 33.3 million subscribers. If you must, Office 2019 is available for purchase. But Office 365 is really what the company wants you to buy.
This of course isn’t the first time that Microsoft has compared its on-premises version of Office to its cloud-powered cousin. But this year, the company is hoping to win over enterprises to the cloud with AI features.
Here is Microsoft 365 corporate vice president Jared Spataro comparing the two (emphasis ours):
Office 365 includes fully-installed Office applications — the latest versions of Word, Excel, PowerPoint, and Outlook. But those apps keep getting better over time, with new capabilities delivered every month. Most importantly, Office 365 is connected to the cloud, so you can access your content from any device, coauthor with anyone in real-time (regardless of whether or not they’ve purchased a copy of Office) and use the power of artificial intelligence (AI) to create impactful content with less effort. On the flipside, Office 2019 also delivers full installs of the Office apps we know and love — but they’re “frozen in time.” They don’t ever get updated with new features, and they’re not cloud-connected. Also, Office 2019 doesn’t support real-time coauthoring across apps, and it doesn’t have the amazing AI-powered capabilities that come with Office 365.
Microsoft could offer these AI features in Office 2019. But it’s the cloud that makes them possible, and Office 365 is the cloud version of the productivity suite.
In other words, “if the cloud hasn’t won you over yet, we hope AI will.” Posted by Stu WisePosted : 06:54 AM
post comment
Friday 30th ,March 2018 City of Atlanta-Suckered into Ransomware. The moral of the story....implement basic security and this won't be your problem. Some of the best practices include:
1. Don't map drive letters. Use UNCs like \\filesevername\sharename
2. Don't click on a link unless you already know EXACTLY what it is and were expecting it.
3. ALWAYS have backups. Daily backups and Weekly Backups.
Atlanta could have simply restored from backup if they had done this simple thing.
-Stu
Atlanta still battling effects of ransomware attack

For over a week, the City of Atlanta has battled a ransomware attack that has caused serious digital disruptions in five of the city's 13 local government departments. The attack has had far-reaching impacts—crippling the court system, keeping residents from paying their water bills, limiting vital communications like sewer infrastructure requests, and pushing the Atlanta Police Department to file paper reports for days. It's been a devastating barrage—all caused by a standard, but notoriously effective strain of ransomware called SamSam.
"It’s important to understand that our overall operations have been significantly impacted and it will take some time to work through and rebuild our systems and infrastructure," a spokesperson for the City of Atlanta said in a statement on Thursday.
Atlanta faces a tough opponent in cleaning up this mess. While dozens of serviceable ransomware programs circulate at any given time, SamSam and the attackers who deploy it are particularly known for clever, high-yield approaches. The specific malware and attackers—combined with what analysts see as lack of preparedness, based on the extent of the downtime—explain why the Atlanta infection has been so debilitating.
'The most interesting thing about SamSam isn't the malware, it's the attackers.'
Jake Williams, Rendition Infosec
First identified in 2015, SamSam's advantages are conceptual as well as technical, and hackers make hundreds of thousands, even millions of dollars a year by launching SamSam attacks. Unlike many ransomware variants that spread through phishing or online scams and require an individual to inadvertently run a malicious program on a PC (which can then start a chain reaction across a network), SamSam infiltrates by exploiting vulnerabilities or guessing weak passwords in a target's public-facing systems, and then uses mechanisms like the popular Mimikatz password discovery tool to start to gain control of a network. This way, the attack doesn't need to rely on trickery and social engineering to infect victims. And SamSam has been adapted to exploit a variety of vulnerabilities in remote desktop protocols, Java-based web servers, File Transfer Protocol servers, and other public network components.
Attackers deploying SamSam are also known to choose their targets carefully—often institutions like local governments, hospitals and health records firms, universities, and industrial control services that may prefer to pay the ransom than deal with the infections themselves and risk extended downtime. They set the ransoms—$50,000 in the case of Atlanta—at price points that are both potentially manageable for victim organizations and worthwhile for attackers.
And unlike some ransomware infections that take a passive, scattershot approach, SamSam assaults can involve active oversight. Attackers adapt to a victim's response and attempt to endure through remediation efforts. That has been the case in Atlanta, where attackers proactively took down their payment portal after local media publicly exposed the address, resulting in a flood of inquiries, with law enforcement like the FBI close behind.
"The most interesting thing about SamSam isn't the malware, it's the attackers," says Jake Williams, founder of the Georgia-based security firm Rendition Infosec. "Once they enter a network, they move laterally, spending time getting positioned before they start encrypting machines. Ideally organizations will detect them before they start the encryption, but that clearly wasn't the case" in Atlanta.
Hackers using SamSam have so far been careful about hiding their identities and covering their tracks. A February report by the threat intelligence firm Secureworks—which is now working with the City of Atlanta to remediate the attack—concluded that SamSam is deployed by either one specific group or a network of related attackers. But little else is known about the hackers in spite of how actively they've targeted institutions around the country. Some estimates say that SamSam has already collected almost $1 million since just December—thanks to a rash of attacks at the beginning of the year. The total largely depends on the fluctuating value of Bitcoin.
In spite of all of this, security best practices—keeping all systems patched, storing segmented backups, and having a ransomware preparedness plan—can still offer real protections against SamSam infection.
"Ransomware is dumb," says Dave Chronister, founder of the corporate and government defense firm Parameter Security. "Even a sophisticated version like this has to rely on automation to work. Ransomware relies on someone not implementing basic security tenets." Posted by Stu WisePosted : 01:52 PM
post comment
Sunday 26th ,November 2017 Support Keeping Network Neutrality Please contact your representatives to put pressure on FCC Chairman Ajit Pai to KEEP Network Neutrality.
For those who don't understand, the FCC wants to remove the rule that keeps
internet service providers from blocking sites just because they don't want you
to see them.
Like when:
In 2005 Madison River Communications blocked all Voice over IP telephone
services until Network Neutrality stopped them.
In 2005 Comcast denied access to P2P service until Network Neutrality
stopped them.
In 2007 ATT blocked SKYPE and over Voice over IP because it competed
with their cell service.
In 2011 MetroPCS blocked all streaming except YouTube until Network
Neutrality stopped them.
In 2013 ATT, SPrint and Verizon blocked access to Google Wallet because
it competed with their Cyber Money offerings.
In 2013 Verizon said the ONLY THING that stopped them from blocking
content they didnt like was because netowrk neutrality rules were in place.
It is likely your bill will look like below...you would have to pay the same $29
you do today for DSL, and then more money if you want fast Netflix, or want fast
Google Mail. Call your Representatives and Senators to put pressure on FCC
to leave the rule alone.

Posted by Stu WisePosted : 10:43 AM
post comment
Sunday 23rd ,April 2017 Microsoft has announced that those who made a one-off purchase of an Office product will no longer get access to OneDrive and Skype Microsoft has announced that those who made a one-off purchase of an Office product will no longer get access to OneDrive and Skype
In a bid to further persuade users of the standalone versions of Office to shift over to a cloud subscription (Office 365), Microsoft has announced that those who made a one-off purchase of an Office product will no longer get access to the business flavours of OneDrive and Skype come the end of the decade.
So here, we are talking about folks who have bought a standalone copy of Office 2016 or previous versions of the suite. Currently, these users can access and make use of both OneDrive for Business and Skype for Business.
However, on October 13, 2020 – which is the date for the end of mainstream support for Office 2016 – these users will have their access to both OneDrive and Skype business services cut off.
In other words, Microsoft wants you to switch over from a standalone product to an Office 365 subscription in order to keep these benefits.
http://www.techradar.com/news/microsoft-is-pushing-office-2016-users-towards-office-365
Posted by Stu WisePosted : 09:29 AM
post comment
Saturday 15th ,April 2017 Bought new PC? MS Wont let you put anything older than Win10 on it! Bought new PC? MS Wont let you put anything older than Win10 on it!
The Redmond giant is no longer serving software fixes to PCs and other systems that run Windows 7 or Windows 8.1 on Intel's fresh new Kaby Lake or AMD's hot-off-the-fab Ryzen chips. Those machines will now be required to update to Windows 10 in order to obtain future improvements.
Microsoft argues this is all because it can't be bothered supporting the latest silicon, such as Intel's 7th-gen Core series, on anything other than Windows 10. To us, it looks like a convenient way of forcing people onto the newest build of its operating system.
Embarrassingly, Redmond's update code has locked out some sixth-generation AMD Carrizo chips and reportedly some recent-ish Intel CPUs, even though those components are still eligible for bug fixes and tweaks for Windows 7 and 8. Microsoft is working on resolving this, apparently. Posted by Stu WisePosted : 08:30 PM
post comment
Sunday 21st ,August 2016 Windows 10 Anniversary Update - update now? -No Windows 10 Anniversary Update - update now? -No

Quick answer is still no. Here are the updated reasons why:
1. We really don’t know where Microsoft is heading with Windows 10. Nobody has come out and said Win10 will be supported by advertising or by add-ons or by sales of harvested data. All we know for sure is that, “once a Windows device is upgraded to Windows 10, we will continue to keep it current for the supported lifetime of the device -- at no additional charge.”
Well, that’s what Windows honcho Terry Myerson promised us on Jan. 21, 2015. Of course, the same person promised us on Oct. 29, 2015, that Win7 and 8.1 customers “can specify that you no longer want to receive notifications of the Windows 10 upgrade through the Windows 7 or Windows 8.1 settings pages." That promise didn’t come true until a few weeks before the marched upgrade stopped. On Sept. 28, 2015, he promised, “Windows 10 collects information so the product will work better for you. You are in control with the ability to determine what information is collected.” That one’s never come close.
2. The march to forced updates continues...
How important is it to control updates on your machine? You need look no further than the “Get Windows 10” campaign, which pushed enormous numbers of Windows 7 and 8.1 users to Windows 10 -- whether or not they understood what they were doing.
3. Start menu is getting worse, not better
Windows 8.1 fans have no reason to gripe, but if you’re on Windows 7, and you’ve learned how to use (and customize!) the Win 7 Start menu, Win10 is a big step down. The Anniversary Update doesn’t make it any better.
4. Ads all over the place!
The only ad Windows 7 and 8.1 customers have had to fend off is the one for Windows 10. Imagine a world in which you could be poked by ads all day, every day. Right now, we’re getting ads on the lock screen and from the Suggested item in the Start menu, along with the odd toaster notification and a slew of default live tiles with ads out the wazoo.
5. Universal Windows apps continue to underwhelm
Several times every month we hear about companies pulling their apps from the Windows Store; Amazon, Tumblr, and PayPal are the most recent big defectors. Besides, those who want the real experience can usually run to the website in their favorite browser.
6. Microsoft Edge, (the new browser) still has all sorts of problems. The small handful of extensions are buggy and severely limited. It’s inherited many of the security holes prevalent in Internet Explorer. Microsoft claims it’s easier on the battery than Firefox or Chrome, which may be a convincing reason to switch, if battery drain in the browser concerns you.
7. Privacy concerns are getting worse, not better
Privacy was, and continues to be, a major concern for Windows 10 customers -- particularly for those who aren’t connected to a corporate network. Microsoft has published a metric ton of web pages about its privacy policies and procedures. What they haven’t published is a simple list of the data they collect as part of their ongoing “telemetry” efforts.
Posted by Stu WisePosted : 09:20 PM
post comment
Wednesday 27th ,July 2016 You can't turn off Cortana in the Windows 10 Anniversary Update In a never-ending story about Windows 10 and the reasons you don't want it...Cortana the ever listening 'assistant' in Windows 10 can not be turned off. I suspect this is capturing even more data and sending it over the internet. Just to review, here is why to switch to Linux, or just keep your Windows 7...
1. MS forcing people to "upgrade" to Windows 10. Upgrades should be YOUR choice.
2. Windows 10 has been shown to capture what you are typing on the keyboard (like passwords) and writes them to files that it transmits to servers on the internet that DON'T belong to Microsoft.
3. Many speculated this mandatory "upgrade" was so that MS would change to a rental model, where you don't own Windows, you instead pay, say, $20 a month to have Windows. MS already has done this for Windows 10 Enterprise where big companies now have to pay $7 a month for the 10's of thousands of copies they have.
Switch to Linux MINT. It has a nice windows 7 style interface and has every thing you need for NO CHARGE! -Stu
You can't turn off Cortana in the Windows 10 Anniversary Update
Microsoft made an interesting decision with Windows 10’s Anniversary Update, which is now in its final stages of development before it rolls out on August 2.
Cortana, the personal digital assistant that replaced Windows 10’s search function and taps into Bing’s servers to answer your queries with contextual awareness, no longer has an off switch.
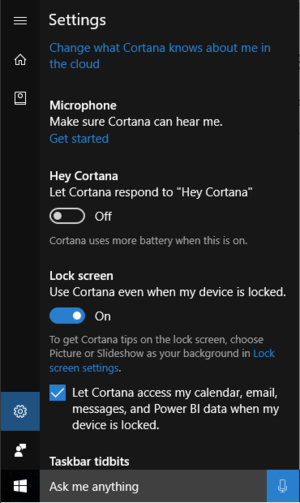
Cortana’s settings in the Anniversary Update.
The impact on you at home: Similar to how Microsoft blocked Google compatibility with Cortana, the company is now cutting off the plain vanilla search option. That actually makes a certain of amount of sense. Unless you turned off all the various cloud-connected bits of Windows 10, there’s not a ton of difference between Cortana and the operating system's basic search capabilities.
Microsoft even says as much: "With the Windows 10 Anniversary Update, the search box is now Cortana," Microsoft said in a statement. "Customers can expect the same great search experience powered by Bing and Microsoft Edge with the added benefit of Cortana’s personality."
In fact, the biggest functional difference is that Cortana is far more useful than plain search thanks to the digital assistant's handy voice commands, reminders, the ability to send text messages, and so on. That said, Microsoft’s move is probably less about the practical differences between Cortana and search, and more about pushing people to use Cortana.
But what if you still don’t want to use Cortana at all?
Refusing to download the Anniversary Update is not an option. You can delay it, but since Windows 10 updates are mandatory for home users, you’ll eventually receive the update.
"Cortana works best when you sign in, but if you choose not to, you can still use her to chat, search the web and your Windows device," Microsoft told PCWorld. "If you like, you can also easily hide Cortana and the search box in the taskbar altogether."
Set limits on Cortana
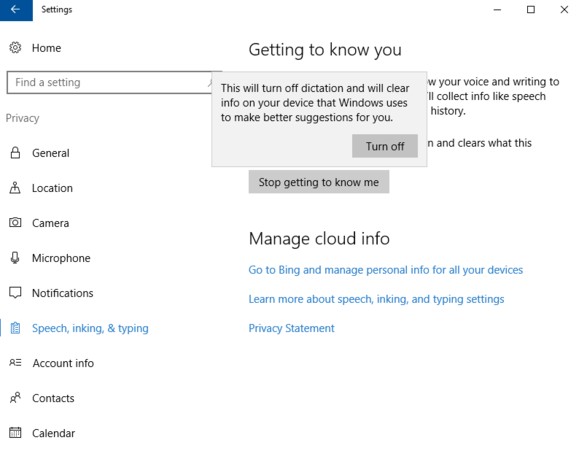
The privacy section of the Settings app in the Anniversary Update
You can also take a few steps to limit Cortana's reach on your system. First, head to Start > Settings > Privacy > Speech, inking, & typing. Now click on Stop getting to know me and then select Turn off. This effectively makes Cortana deaf to the sound of your voice as well as blind to your typing history and—for stylus wielders— handwriting patterns. It also turns off system-wide dictation.
If you're going to keep the search box on your taskbar open Cortana and then click on the settings cog in the lower-right corner. On Cortana’s settings screen, disable every slider that can be set to Off, such as search history and device history. That helps prevent some data usage and tracking, but Cortana will still be working.
To wipe Cortana's memory of you, click on Change what Cortana knows about me in the cloud, which is at the very top of the settings panel. On the next screen, scroll down to the bottom and click Clear. This orders Microsoft to delete any information it has saved about you via Cortana, including personal interests, browsing history, and so on. If you're going to use Cortana but feel uneasy about its data collection you should clear this option periodically.
You can even get rid of Cortana's presence entirely, as Microsoft said. To do this right-click on the Cortana search box, and select "Hidden". Doing so, however, apparently makes the Cortana box disappear without any obvious way of getting her back. (Note that if you leave "Hey Cortana" turned on, the Cortana box will re-appear when you say those words.)
After that’s done you can also go to Bing Maps to edit your saved places (if you have any) as well as Bing’s search history page to clear information stored about your search habits.
Use an alternative
Everything
If you’re still unsatisfied after you’ve crippled as much of Cortana as possible, consider ditching it completely and going with a third-party system search utility instead. If you aren’t using Cortana's web-connected features all you really need is file and folder search, anyway.
One of our favorite third-party search tools is Everything. This wonderful donationware is small, simple, easy to use, and (most importantly) fast. You can also pin Everything to your taskbar to make searching as easy as Microsoft’s built-in solution.
Of course, another alternative is to dump Windows 10 altogether and switch to Linux. That’s certainly a valid alternative—as commenters on this article will no doubt mention before long. PCWorld's guide to the best Linux distros for beginners and Windows XP refugees can help get you up to speed if you decide to opt for that drastic solution.
Posted by Stu WisePosted : 03:11 PM
post comment
Thursday 11th ,February 2016 Harvard Says Dont Ban Encryption An actual Harvard study confiroms what everyone knows....if the US demands 'back doors' into encryption, the business will just be pushed off shore. Now I get that politicians are frequently 'tech' illiterate, but this shouldn't be that complicated. someone just use the example to them of :
"Why don't you leave the keys to your house hanging down at the local police station so they can get into your house when they need to?"
Everyone knows its because some unscrupulous person will steal the police station keys or a city employee might be bribed to 'lend' them out! -Stu
--------------------------------------------------------------------------
After a two-year campaign from the FBI, U.S. intelligence officials, and powerful politicians calling for backdoor access into Americans’ encrypted data, a new Harvard study argues that encryption is a worldwide technology that the United States cannot regulate and control on its own.
The study, titled “A Worldwide Survey of Encryption Products,” aimed to catalog all the encryption products available online today. Researchers identified 546 encryption products from developers outside the U.S., a number representing two-thirds of the 865 that are available worldwide. The point of the research is clear: There’s a whole world of cryptography outside the United States. Any U.S. law that mandates so-called “backdoors” in encryption technology—Sen. Richard Burr (R-N.C.) is currently writing a bill that may do just that—will just push the business outside American borders.
“If U.S. products are all backdoored by law, I guarantee you stuff coming out of Finland is going to make a big deal of that.”
The migration has already begun. Silent Circle, an encrypted communications company started in America, made the move to Switzerland in 2014 to avoid American government attempts to access their data.
Open-source projects that have their code freely available online and whose developers and supports are spread out across the world may be more “jurisdictionally agile” and able to move toward countries, like the Netherlands, that disavow backdoors, the study found. The new study is authored by independent and Harvard researchers Bruce Schneier, Kathleen Seidel, and Saranya Vijayakumar.
The researchers expect non-U.S. tech companies to take advantage of any anti-encryption policy to come out of America.
“The potential of an NSA-installed backdoor in U.S. encryption products is rarely mentioned in the marketing material for the foreign-made encryption products,” the study explains. “This is, of course, likely to change if U.S. policy changes.”
“If U.S. products are all backdoored by law, I guarantee you stuff coming out of Finland is going to make a big deal of that,” Schneier told the Daily Dot.
Despite pretensions about the superiority of American-made technology, non-U.S. encryption products are just as good as American made software, the study concluded.
“Cryptography is very much a worldwide academic discipline, as evidenced by the quantity and quality of research papers and academic conferences from countries other than the U.S. Both recent [National Institute of Standards and Technology] encryption standards—AES and SHA-3—were designed outside of the US, and the 4 submissions for those standards were overwhelmingly non-US. Additionally, the seemingly endless stream of bugs and vulnerabilities in US encryption products demonstrates that American engineers are not better their foreign counterparts at writing secure encryption software. Finally, almost all major U.S. software developers have international teams of engineers, both working in the U.S. and working in non-U.S. offices.”
FBI Director James Comey, the leading voice in the campaign against strong encryption, agrees with some of what the study concludes. Last year, Comey said the solution to “going dark” was to construct a legal regime spanning North America, Europe, and China that requires tech companies to build backdoors for governments into their products, effectively acknowledging that changes to U.S. law are not enough to stymie increased use of encrypted technology.
Thanks to stalwart rhetoric from Comey and other state and federal authorities, the debate over encryption has reached a new intensity in the last year. Across the divide, a virtual consensus of technologists from academia, industry, and civil society argue that backdoors into encryption will harm both the cybersecurity and privacy rights of Americans.
"So let me be crystal clear: Weakening encryption or taking it away harms good people who are using it for the right reason," Apple CEO Tim Cook, one of the most vocal and powerful defenders of encryption, said in 2015.
Even former NSA chief Michael Hayden stands firmly against government backdoors into encryption.
But powerful figures like Comey and Manhattan District Attorney Cyrus Vance, Jr. have been vocal opponents of the rising popularity of encryption.
Apple's “unilateral decision” to encrypt iPhones will harm American national security by allowing “homegrown violent extremists and terrorists to communicate with each other, to send messages without law enforcement being able to identify what they’re saying,” Vance argued last year.
Because they encrypt data on the device, he added, iPhones are going to be "the terrorists community device of choice." Posted by Stu WisePosted : 12:01 PM
post comment
Thursday 21st ,January 2016 Deliberately hidden backdoor account in several meeting equipment packages With state governments like California, and Massachusetts demanding backdoors into your cell phone encryption, it is amusing to see how offended our government is to find that the same tech is present in products they purchased! -Stu
About the vendor: "AMX (www.amx.com) is part of the HARMAN Professional Division, and the leading brand for the business, education, and government markets for the company. As such, AMX is dedicated to integrating AV solutions for an IT World. AMX solves the complexity of managing technology with reliable, consistent and scalable systems comprising control and automation, system-wide switching and AV signal distribution, digital signage and technology management. AMX systems are deployed worldwide in conference rooms, homes, classrooms, network operation/command centers, hotels, entertainment venues and broadcast facilities, among others." Source: http://www.amx.com/automate/aboutamx.aspxTo be fair, their products really do offer a wide variety of features, which is probably also the reason why US President Barrack Obama is sometimes seen in front of a control panel by AMX, while sitting in a meeting at the White House. According to the case studies published by AMX they have multiple governmental and military bodies equipped with their conference room gear. This includes but is not limited to the White House, the U.S. Forces Afghanistan as well as the Center for Strategic and International Studies (CSIS).Some of the affected devices seem to be "tested and approved by the US DoD as a JITC certified secure command and control, conference, training and briefing room solution" as well according to this AMX web page. Further AMX market customer profiles can be accessed here: AMX customer profiles
With that said, lets talk about security.
How AMX (HARMAN Professional) handles security.In early 2015 SEC Consult decided to take a look into the security of a conference room solution provided by AMX. Let's not waste any words on the tiring process of getting the binaries out of the small black box and jump right to the meat of it all.During the analysis of the authentication procedure of one of the central controller systems (AMX NX-1200), something strange popped up:
 |
| IDA excerpt: "setUpSubtleUserAccount" function | A function, which they decided to call "setUpSubtleUserAccount". And this function does exactly what the name would suggest.It sets up a subtle user account. The strings seen in the above screenshot, revealed an interesting detail about the vendor's security strategy. AMX apparently called for a little extra help in the universe of Marvel superheroes to protect their products (and coincidentally also the U.S. military) from the evil super villain hackers. At least that is what we assume, because the expert spy and top S.H.I.E.L.D. agent Black Widow has her own personalized account on the device.
"Natasha Romanova, known by many aliases, is an expert spy, athlete, and assassin. Trained at a young age by the KGB's infamous Red Room Academy, the Black Widow was formerly an enemy to the Avengers. She later became their ally after breaking out of the U.S.S.R.'s grasp, and also serves as a top S.H.I.E.L.D. agent"
Like most superheroes, Black Widow prefers to stay under the radar, not requesting any credit for her heroic actions. Because of that, the vendor made an effort in hiding her details from eyes of innocent admins and users alike:
 |
| AMX Master Configuration Manager: Black Widow backdoor account is hidden and does not show up anywhere | As the daily work of a superhero, especially for an IT SECURITY SUPERHERO, is quite challenging, AMX went ahead and implemented some additional tools like a packet-capture/sniffing facility, to aid the expert spy Black Widow in the fight against the super villain hackers. These tools are only available to our superhero as the power they hold should not be available to simple administrators.
Responsible disclosureAs usual, SEC Consult Vulnerability Lab communicated this issue according to our responsible disclosure policy. Initial contact and exchange of the security advisory was performed through the European sales team at AMX. About seven months(!) later AMX provided a fix for the backdoor. A quick review of the new firmware showed that the backdoor was still in place, but Black Widow was gone. Did she decide to step down after being exposed? Did they fire her? Unfortunately we don't have any details on this.
Whatever the reason may be, the vendor decided to hire somebody from the DC universe this time. Na na na na na na na na ... you guessed it. BATMAN! But not the usual Batman, the leet-hacker-Batman, who uses numbers and special characters to write his own name:
 |
| IDA excerpt: New backdoor username 1MB@tMaN |
This time around, we decided (tried) to get in direct contact with somebody responsible for security at AMX (HARMAN Professional). After numerous emails requesting a security contact to exchange the information about the vulnerability, finally somebody replied. We exchanged the security advisory unencrypted, as requested by AMX. Then they went silent again.Fast forward another three months to early 2016, we had still not heard back from AMX, despite asking for a status update several times, and even postponing the release of the security advisory in order to give them (even) more time for sorting things out with Batman and Black Widow.Yesterday (2016-01-20) AMX finally replied, informing SEC Consult that they have released firmware updates for the affected products. These updates are untested and unconfirmed by SEC Consult.Grab them here while they're hot: http://www.amx.com/techcenter/NXSecurityBrief/ - we were told that some of the updates can only be retrieved through AMX tech support.Furthermore, our contact stated that AMX will be starting a major security initiative which is a very good thing to do!
For the tech geeks, here is our advisory with additional technical information, a contact timeline detailing the communication attempts and a list of affected devices. Posted by Stu WisePosted : 09:39 PM
post comment
Thursday 31st ,December 2015 Spying on Congress and Israel: NSA Cheerleaders Discover Value of Privacy Only When Their Own Is Violated Gotta love it....Rep Hoekstra poo-poo'd our concerns about the NSA spying on us (U.S) but NOW is "outraged" because the NSA was spying on HIM!
-Stu
Glenn Greenwald
The Wall Street Journal reported yesterday that the NSA under President Obama targeted Israeli Prime Minister Benjamin Netanyahu and his top aides for surveillance. In the process, the agency ended up eavesdropping on “the contents of some of their private conversations with U.S. lawmakers and American-Jewish groups” about how to sabotage the Iran Deal. All sorts of people who spent many years cheering for and defending the NSA and its programs of mass surveillance are suddenly indignant now that they know the eavesdropping included them and their American and Israeli friends rather than just ordinary people.
The long-time GOP chairman of the House Intelligence Committee and unyielding NSA defender Pete Hoekstra last night was truly indignant to learn of this surveillance:
In January 2014, I debated Rep. Hoekstra about NSA spying and he could not have been more mocking and dismissive of the privacy concerns I was invoking. “Spying is a matter of fact,” he scoffed. As Andrew Krietz, the journalist who covered that debate, reported, Hoekstra “laughs at foreign governments who are shocked they’ve been spied on because they, too, gather information” — referring to anger from German and Brazilian leaders. As TechDirt noted, “Hoekstra attacked a bill called the RESTORE Act, that would have granted a tiny bit more oversight over situations where (you guessed it) the NSA was collecting information on Americans.”
But all that, of course, was before Hoekstra knew that he and his Israeli friends were swept up in the spying of which he was so fond. Now that he knows that it is his privacy and those of his comrades that has been invaded, he is no longer cavalier about it. In fact, he’s so furious that this long-time NSA cheerleader is actually calling for the criminal prosecution of the NSA and Obama officials for the crime of spying on him and his friends.
This pattern — whereby political officials who are vehement supporters of the Surveillance State transform overnight into crusading privacy advocates once they learn that they themselves have been spied on — is one that has repeated itself over and over. It has been seen many times as part of the Snowden revelations, but also well before that.
In 2005, the New York Times revealed that the Bush administration ordered the NSA to spy on the telephone calls of Americans without the warrants required by law, and the paper ultimately won the Pulitzer Prize for doing so. The politician who did more than anyone to suffocate that scandal and ensure there were no consequences was then-Congresswoman Jane Harman, the ranking Democratic member on the House Intelligence Committee.
Former Congresswoman Jane Harman, D-Calif., in 2010.
Photo: Lauren Victoria Burke/AP
In the wake of that NSA scandal, Harman went on every TV show she could find and categorically defended Bush’s warrantless NSA program as “ both legal and necessary,” as well as “ essential to U.S. national security.” Worse, she railed against the “despicable” whistleblower (Thomas Tamm) who disclosed this crime and even suggested that the newspaper that reported it should have been criminally investigated (but not, of course, the lawbreaking government officials who ordered the spying). Because she was the leading House Democrat on the issue of the NSA, her steadfast support for the Bush/Cheney secret warrantless surveillance program and the NSA generally created the impression that support for this program was bipartisan. But in 2009 — a mere four years later — Jane Harman did a 180-degree reversal. That’s because it was revealed that her own private conversations had been eavesdropped on by the NSA. Specifically, CQ’s Jeff Stein reported that an NSA wiretap caught Harman “telling a suspected Israeli agent that she would lobby the Justice Department to reduce espionage charges against two officials of American Israeli Public Affairs Committee (AIPAC) in exchange for the agent’s agreement to lobby Nancy Pelosi to name Harman chair of the House Intelligence Committee.” Harman vehemently denied that she sought this quid pro quo, but she was so furious that she herself(rather than just ordinary citizens) had been eavesdropped on by the NSA that — just like Pete Hoekstra did yesterday — she transformed overnight into an aggressive and eloquent defender of privacy rights, and demanded investigations of the spying agency that for so long she had defended:
I call it an abuse of power in the letter I wrote [Attorney General Eric Holder] this morning. … I’m just very disappointed that my country — I’m an American citizen just like you are — could have permitted what I think is a gross abuse of power in recent years. I’m one member of Congress who may be caught up in it, and I have a bully pulpit and I can fight back. I’m thinking about others who have no bully pulpit, who may not be aware, as I was not, that someone is listening in on their conversations, and they’re innocent Americans.
The stalwart defender of NSA spying learned that her own conversations had been monitored and she instantly began sounding like an ACLU lawyer, or Edward Snowden. Isn’t that amazing?
The same thing happened when Dianne Feinstein — one of the few members of Congress who could compete with Hoekstra and Harman for the title of Most Subservient Defender of the Intelligence Community (“I can honestly say I don’t know a bigger booster of the CIA than Senator Feinstein,” said her colleague Sen. Martin Heinrich) — learned in 2014 that she and her torture-investigating Senate Committee had been spied on by the CIA. Feinstein — who, until then, had never met an NSA mass surveillance program she didn’t adore — was utterly filled with rage over this discovery, arguing that “the CIA’s search of the staff’s computers might well have violated … the Fourth Amendment.” The Fourth Amendment! She further pronounced that she had “grave concerns” that the CIA snooping may also have “violated the separation of powers principles embodied in the United States Constitution.”
During the Snowden reporting, it was common to see foreign governments react with indifference — until they learned that they themselves, rather than just their unnotable subjects, were subject to spying. The first reports we did in both Germany and Brazil were about mass surveillance aimed at hundreds of millions of innocent people in those countries’ populations, and both the Merkel and Rousseff governments reacted with the most cursory, vacant objections: It was obvious they really couldn’t have cared less. But when both leaders discovered that they had been personally targeted, that was when real outrage poured forth, and serious damage to diplomatic relations with the U.S. was inflicted.
So now, with yesterday’s WSJ report, we witness the tawdry spectacle of large numbers of people who for years were fine with, responsible for, and even giddy about NSA mass surveillance suddenly objecting. Now they’ve learned that they themselves, or the officials of the foreign country they most love, have been caught up in this surveillance dragnet, and they can hardly contain their indignation. Overnight, privacy is of the highest value because now it’s their privacy, rather than just yours, that is invaded.
What happened to all the dismissive lectures about how if you’ve done nothing wrong, then you have nothing to hide? Is that still applicable? Or is it that these members of the U.S. Congress who conspired with Netanyahu and AIPAC over how to sabotage the U.S. government’s Iran Deal feel they did do something wrong and are angry about having been monitored for that reason?
I’ve always argued that on the spectrum of spying stories, revelations about targeting foreign leaders is the least important, since that is the most justifiable type of espionage. Whether the U.S. should be surveilling the private conversations of officials of allied democracies is certainly worth debating, but, as I argued in my 2014 book, those “revelations … are less significant than the agency’s warrantless mass surveillance of whole populations” since “countries have spied on heads of state for centuries, including allies.”
But here, the NSA did not merely listen to the conversations of Netanyahu and his top aides, but also members of the U.S. Congress as they spoke with him. And not for the first time: “In one previously undisclosed episode, the NSA tried to wiretap a member of Congress without a warrant,” the New York Times reported in 2009.
The NSA justifies such warrantless eavesdropping on Americans as “incidental collection.” That is the term used when it spies on the conversations of American citizens without warrants, but claims those Americans weren’t “targeted,” but rather just so happened to be speaking to one of the agency’s foreign targets (warrants are needed only to target U.S. persons, not foreign nationals outside of the U.S.).
This claim of “incidental collection” has always been deceitful, designed to mask the fact that the NSA does indeed frequently spy on the conversations of American citizens without warrants of any kind. Indeed, as I detailed here, the 2008 FISA law enacted by Congress had as one of its principal, explicit purposes allowing the NSA to eavesdrop on Americans’ conversations without warrants of any kind. “The principal purpose of the 2008 law was to make it possible for the government to collect Americans’ international communications — and to collect those communications without reference to whether any party to those communications was doing anything illegal,” the ACLU’s Jameel Jaffer said. “And a lot of the government’s advocacy is meant to obscure this fact, but it’s a crucial one: The government doesn’t need to ‘target’ Americans in order to collect huge volumes of their communications.”
Whatever one’s views on that might be — i.e., even if you’re someone who is convinced that there’s nothing wrong with the NSA eavesdropping on the private communications even of American citizens, even members of Congress, without warrants — this sudden, self-interested embrace of the value of privacy should be revolting indeed. Warrantless eavesdropping on people who have done nothing wrong — the largest system of suspicionless mass surveillance ever created — is inherently abusive and unjustified, and one shouldn’t need a report that this was done to the Benjamin Netanyahus and Pete Hoekstras of the world to realize that. Posted by Stu WisePosted : 08:37 AM
post comment
Friday 11th ,December 2015 Windows 10 upgrades reportedly appearing as mandatory for some users They say there is NO free lunch, and Windows 10 is no exception.
MS is supposedly 'giving it away' but most folks don't like the personal information that the OS is doing sending to locations on the internet which
are NOT Microsoft. Other folks feel this is a way of forcing people to have a software which will eventually force them to use a 'rental' version of Windows
that you would never own....only rent! Might be time to try Kubuntu 15.04 - KDE Plasma 5.2 Desktop Linux? -Stu
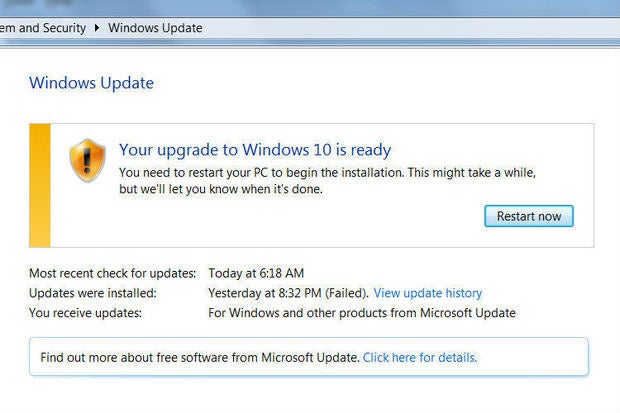 Credit: Josh Mayfield Credit: Josh Mayfield
Microsoft is reportedly making it harder for Windows 7 and Windows 8.1 users to avoid the upgrade to Windows 10.
Some users now claim that they no longer see an option in the Control Panel to install updates to their current version of Windows. Instead, a message says that the “upgrade to Windows 10 is ready,” and prompts users to “restart your PC to begin the installation.”
Another user claims to have seen a countdown timer for installing Windows 10, with an option to reschedule but no way to call off the upgrade entirely.
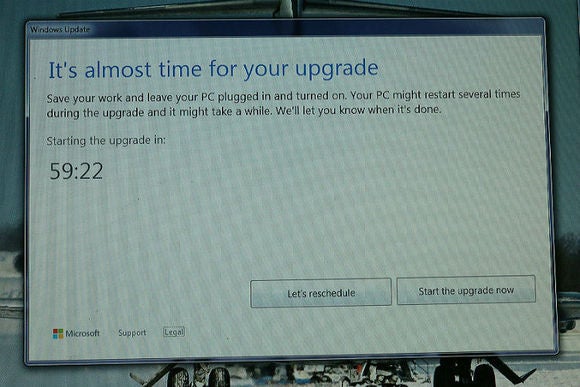
Both upgrade tactics were reported by Josh Mayfield, whose GWX Stopper program is designed to eliminate Microsoft’s Windows 10 update notifications.
In a blog post, Mayfield said GWX Stopper can’t help users who’ve seen either of the above dialogs. (The post was first spotted by ZDNet.) If the reports are accurate and not due to user error of some kind, it’s yet another case of Microsoft trying to ramp up Windows 10 adoption by coercion rather
than incentive. Microsoft has previously confirmed that it automatically downloads Windows 10 installation files
without users’ permission, occupying as much as 6GB of storage space in a hidden folder. Slyly executing the installation would be the next logical step.
We’ve reached out to Microsoft for comment, but have yet to hear a response.
Why this matters: For most people, Windows 10 should be an improvement over previous versions, but there are plenty of users who have
perfectly valid reasons not to upgrade. Microsoft likes to talk about how it wants people to love Windows,
but that’s not something you can force.
This story, "Windows 10 upgrades reportedly appearing as mandatory for some users" was originally published by PCWorld. Posted by Stu WisePosted : 06:25 PM
post comment
Wednesday 2nd ,December 2015 Storage in the Cloud - What are the good Choices Cloud Storage Solutions are a really handy way of sharing files amongst the various IT devices you have. The qualities you should look for are:
1. Support for all of the devices you have and those you have not yet bought. I recommend covering your phone, PC and your tablets. Make sure you get Android or Apple iOS support, Windows, Mac, or Linux.
2. Amount of Free space in the 'Free' plans. Some plans offer free space but only for a limited amount of time. 3. Evaluate the ease of use of the product you select BEFORE you move all your data up there. My favorites here would be Mega with its 50GB free package and Tresorit if you are ok with 3GB free. Mozy as the number 2 choice with 2GB.
You will notice that I did not mention Dropbox here. Although it is encrypted, the encryption take place on the Dropbox servers which means that someone who compromises those servers would be able to get the keys to open your files. Remember that the best encryption is the that which is done on your local machine and YOU control the keys!
-Stu
MEGA
https://mega.nz/

Mega is a New Zealand-based company that was set up by the German-born entrepreneur Kim Dotcom in 2013, who now has no involvement with it. Mega puts its security credentials front and centre. Unlike some of its rivals, this service provides encryption in every part of the process. So anything you send to the cloud is encrypted locally, on-route, and on the destination server. Mega itself doesn’t have any way of accessing your information, as you hold the encryption key. The upshot of all this is that anything you store on Mega is only able to be opened by you. To achieve this there are local clients for Windows, OS X, and Linux, plus there are also secure browser plugins for Chrome and Firefox. Apps are available for iOS, Android, Windows Phone, and even Blackberry.
The standard free package affords a whopping 50GB of space. If this isn't enough you can have 500GB (99 Euros per year), 2TB (199 Euros per year), or 4TB (299 Euros per year) and increased bandwidth with each package so you can share files back and forth with friends.
A few secure communications features are coming in 2016: video chat, voice calling, email and IM. These are encrypted end-to-end, making them more private than Skype or Google Hangouts.
Verdict: With its generous free account, fast service, cross platform appeal, and highly secure nature, Mega is a very good choice for most people looking for an online storage solution.
COPY

Copy has been around for a little while now and is a simple to use alternative to the likes of Dropbox, Onedrive, and Google Drive. In line with Google, Copy starts with a decent 15GB of free space to new users, and this can be increased via a referrals system that rewards both you and any new user with an additional 5GB each (up to a maximum of 25GB extra space). In operation the service works well, with decent speed, and no real issues. Copy also supports versioning, so previous copies of your files are retained after you make changes, and the whole service runs on 256-bit AES encryption that covers data in transit and on the copy servers.
pCloud

https://www.pcloud.com/
pCloud will give you a respectable 10GB of free storage. This can be quickly upgraded to 20GB through the regular incentives such as recommending friends (1GB per person) completing a tutorial (3GB) and various social media links, but the real temptation is the very reasonable prices for the larger storage options. 500GB will set you back around £2.65p/m ($3.99), while 1TB is available for around £5.30p/m ($7.99), There are clients available for Windows, Mac, Linux, iOS and Android, plus you can also access your account via the website. All data transfers between the pCloud servers and your machine are handled with TLS/SSL encryption, so they should be safe on their travels. One of the more specialist features on pCloud is that of a Crypto Folder, into which you can place files that you want to keep away from prying eyes, be they hackers or certain government agencies. The contents of this folder is encrypted locally on your device, and not even pCloud employees can read it without your key. pCloud uses 256-bit AES encryption for the files and folders, while the encryption key uses 4096-bit RSA, meaning that both are very secure. Not all of the files and folders are encrypted automatically, but instead you drag the contents you want to remain private into a dedicated Crypto folder. This means you can have a mixture of encrypted and non-encrypted files on your drive at the same time, handy for sharing non-confidential documents with friends while also having and added level of security for others. The Crypto folder doesn’t come as a standard feature with the storage plans, instead it’s an additional £2.65 ($3.99) p/m, but if you have need of a high security feature then it’s not a big price to pay, plus you can try it out for free thanks to the 14-day trial.
Tresorit

https://tresorit.com/
There are several services that offer secure storage in the cloud, but Tresorit is definitely one of the best. You get 3GB of storage space. One of the reasons that Tresorit is so secure comes down to the way files are encrypted. With a local client installed on either your Windows or OSX machine your data is encrypted locally, then sent, using TLS, to the Tresorit servers where it remain encrypted. You retain the decryption keys (not that you’ll ever see them) and not even the staff at Tresorit can access your files, thanks to their Zero-Knowledge policy.
To add a further level of security you can enable two-step verification, so even if someone steals your laptop or ID, they’ll need your phone to access the data. The servers are also based in the EU and governed by Swiss privacy laws which should keep it out of the hands of any invasive national agencies that feel it is their right to purloin your personal information.
Tresorit hasn’t skimped on the design elements of its UI though, with desktop clients, web portals, and mobile apps ( Windows, Mac, Linux, iOS, Android, Windows Phone or Blackberry) that look good, are simple to use, and perform reliably.
Mozy

http://mozy.com
Mozy offers a very limited free service with 2GB of space and the chance to get more via referrals
Mozy offerings two types of encryption (256-bit AES or a 448-bit Blowfish key) which perform the essential part of encrypting your files while still on your computer, rather than sending them across the internet to the servers to do the job there. The upshot of this is that it is much harder for someone to hijack your information on route to the servers and find anything they can use.
If security is your prime focus then Mozy has a lot to offer. The versioning support is good, local encryption is always our preferred method, and the one click restore option is a nice addition. There’s still work to be done on the design elements though, and 2GB of free storage
SPIDEROAK

https://spideroak.com/
If privacy is a major concern then Spideroak might be the cloud storage service for you. Most of the mainstream offerings all encrypt your data on their servers, but Spideroak has a different approach. Once you’ve set up your account and downloaded the desktop client (Windows, Mac, and Linux are available) you can transfer files to your local folder, which will then encrypt them before syncing them to Spideroak. This might not sound that different, but it means that your data is readable only by you, as the key is local to your machine. Spideroak calls this ‘Zero-knowledge privacy’ as the employees at the company can’t access your data and, by extension, it should also mean any interested government parties would also find it extremely difficult.
Traditionally this would make accessing files from numerous machines more problematic, not to mention sharing with others, but the team has worked ways around that. Spideroak Hive is the control centre of your storage. This app, which runs locally, is very similar to the Dropbox-style of folder on your desktop, although the interface has a little more detail.
A basic free account comes with 2GB of storage, but the snag is that it's only a 60-day trial.
Posted by Stu WisePosted : 06:44 PM
post comment
Thursday 19th ,November 2015 Windows 3.1 Is Still Alive, And It Just Killed a French Airport In all fairness, if it does the job, and isn't a security risk the only problem might be finding a technician who still knows how to work with it! -Stu
November 13, 2015 | 7:30 am
A computer glitch that brought the Paris airport of Orly to a standstill Saturday has been traced back to the airport's "prehistoric" operating system. In an article published Wednesday, French satirical weekly Le Canard Enchaîné (which often writes serious stories, such as this one) said the computer failure had affected a system known as DECOR, which is used by air traffic controllers to communicate weather information to pilots. Pilots rely on the system when weather conditions are poor.
DECOR, which is used in takeoff and landings, runs on Windows 3.1, an operating system that came onto the market in 1992. Hardly state-of-the-art technology. One of the highlights of Windows 3.1 when it came out was the inclusion of Minesweeper — a single-player video game that was responsible for wasting hours of PC owners' time in the early '90s.

Minesweeper on Windows 3.1 (via PCWorld)
DECOR's breakdown on Saturday prevented air traffic controllers from providing pilots with Runway Visual Range, or RVR, information — a value that determines the distance a pilot can see down the runway. As fog descended onto the runway and engineers battled to find the origin of the glitch, flights were grounded as a precaution.
"The tools used by Aéroports de Paris controllers run on four different operating systems, that are all between 10 and 20 years old," explained Alexandre Fiacre, the secretary general of France's UNSA-IESSA air traffic controller union. ADP is the company that runs both Orly and Paris' other airport, Charles de Gaulle, one of the busiest in the world.
"Some of ADP's machines run on UNIX [an operating system favored by universities and start-ups in the '80s], but also Windows XP," said Fiacre, who works as an aviation security systems engineer.

Windows 3.1 file manager (via PCWorld)
"The issue with a system that old is that people don't like to do maintenance work," explained Fiacre. "Furthermore, we are starting to lose the expertise [to deal] with that type of operating system. In Paris, we have only three specialists who can deal with DECOR-related issues," said Fiacre. "One of them is retiring next year, and we haven't found anyone to replace him," he added.
Fiacre compared the challenges of running the Windows 3.1-supported DECOR to the issues faced by NASA with its Voyager program, which was launched in 1977. Voyager 1 and Voyager 2, the two robotic probes that are used by NASA to study the outer solar system, rely on 250 kHz central processing units made by General Electric.
These 40 year-old computers are less powerful than today's pocket calculators, and use out-of-date programming languages like FORTRAN, which means that, with the impending retirement of the last engineer from the original Voyager mission, NASA will soon be recruiting a new expert on 1970s computer programming.

Punched card from a FORTRAN program (via Wikimedia Commons)
French aviation systems engineers face their own maintenance challenges, compounded by the unavailability of spare parts for these outdated machines. "Sometimes we have to go rummaging on eBay to replace certain parts," said Fiacre. "In any case, these machines were not designed to keep working for more than 20 years."
According to Le Canard Enchaîné, France's transport minister has promised that "equipment will be upgraded by 2017." But Fiacre is not so sure about this timeline. "In my opinion, we'll upgrade in 2019 at the earliest, perhaps even in 2021," he said.
Fiacre described Saturday's breakdown as a "warning," but noted that the systems failure had in no way "endangered passengers, since [air traffic] controllers took a number of precautionary measures to eliminate all risk."

The Flying Windows screensaver, which has become synonymous with Windows 3.1 (via PCWorld)
ADP has not yet released a statement concerning Saturday's disruption of air traffic.
The grounding of flights in Paris is not the first incident to highlight the lack of airport resources and the use of outdated systems to ensure safety in the skies, and not just in France.
In December 2014, airspace over London was closed for 36 minutes and some fifty flights were canceled following a computer failure that was later blamed on 50-year-old software.
Earlier this year, two hackers were awarded one million "bug bounty" air miles each by United Airlines after flagging up flaws in the company's web security system.
One person who was put out by Saturday's air traffic disruption is French politician Alain Juppé, one of the contenders in the primaries for the French Republican Party's 2017 presidential nomination. Juppé was due to fly to Paris from the southwestern city of Bordeaux to attend a party conference.
About to take off from Bordeaux, Orly is closed. Unable to get to Republican national council on time. Shame! I had prepared a good speech.
An aviation engineer interviewed by Le Canard Enchaîné Wednesday raised the possibility of similar disruptions during the UN's COP 21 climate change conference, which will be held in Paris, from November 30 to December 11. "Imagine, during COP 21, the comings and goings of heads of state being disrupted because of prehistoric software," he told the weekly. Posted by Stu WisePosted : 10:30 AM
post comment
Homeland Security deports tourists for Twitter jokes Best use caution when tweeting....the walls have ears....
-Stu
Homeland Security deports tourists for Twitter jokes
Are the feds listening to Twitter? Yes, as a British couple found out when Homeland Security locked them up when they landed in Los Angeles.
The British papers are up in arms about the detainment and deportation of Leigh Van Bryan, 26, a bar manager, and his friend Emily Banting, 24. Homeland Security read Bryan's tweets about plans to "destroy America" before he and Banting arrived in Los Angeles. Evidently, the feds aren't up on partying slang used by twenty-somethings in England, where "destroy" can also mean "party like crazy."
Both "potential terrorists" were detained for 12 hours, then shipped back home. Banting's bags were thoroughly searched for digging implements, since Bryan had quoted the Family Guy sitcom and tweeted "3 weeks today, we're totally in LA p****** people off on Hollywood Blvd and diggin' Marilyn Monroe up!" Homeland Security has declined to comment, so let's keep an eye out for #We'reSorry. Posted by Stu WisePosted : 10:20 AM
post comment
Pressure on Google and Apple to open up encryption to government Folks think of it this way...would you be willing to leave the keys to your house or apartment down at the front desk of the police department? Hell no...because you know that some clerk would steal them, loan them to a sketchy friend for $20 who would then rob your house. Tell your representatives this should not happen. -Stu
Manhattan DA steps up pressure on Google and Apple to open up encryption to government

Addressing [PDF] the 6th Annual Financial Crimes and Cybersecurity Symposium yesterday, the DA discusses what he describes as ‘the “going dark” problem facing investigatory services whose subpoenas cannot be obeyed in the cases of companies which provide client-side encryption in devices, and which cannot themselves access their customers’ data. Vance said:
“As a prosecutor, I have no higher public policy priority than to persuade Congress to enact sensible statutes that will protect legitimate privacy concerns, while giving law enforcement the ability to access cellphones when necessary to prosecute serious crimes and fight terrorism. I understand that Apple and Google did not take their actions in a vacuum. The public is angry, and at times understandably angry, at some highly-publicized cases of overreaching in intelligence- gathering. I have no doubt that full-disk encryption is a strong branding and public-relations move for Apple and Google in the wake of Edward Snowden’s disclosures. But ultimately, the line between an individual’s right to privacy and the legitimate needs of law enforcement should not be decided by the marketing departments of smartphone companies. That line should be defined by legislatures and the courts.”
Vance Jr. goes on to explain carefully in his address that ‘lawful access to criminal evidence on smartphones’ is unrelated to the kind of mass-surveillance which he admits has rightly outraged the public in the wake of Edward Snowden’s revelations, and that the warrant requirement now being dodged by full-disk encryption goes back two centuries.
He also discusses a new report from his department, due for release today, which will, he says, provide a solution that is both technologically and politically workable. He cites the recent attacks in Paris as a spark for a new debate about whether zero-knowledge encryption can be permitted to continue. Referring to gestures of support for the victims of the attacks, by Uber and Facebook, Vance Jr. said “I hope the same spirit of public-mindedness will lead smartphone providers to negotiate a solution to this problem.” Discussing what his department is asking for, Vance said:
“Our solution requires no new technology or costly adjustments. In fact, our report makes clear what kind of access we do not seek. We do not want a backdoor for the government. We do not want a “key” held by the government, and we do not want to collect bulk data on anybody. “
So, as far as can be deduced, the request boils down to Google and Apple deactivating zero-knowledge encryption for the Android and iOS mobile operating systems, respectively.
Comment It is difficult to see how Vance Jr.’s request occupies the ‘rare middle ground’ that he has claimed in his speech. Rather it seems to be a repeat of the same governmental complaint that has been sounded out at measured and carefully-timed intervals ever since Apple – not the innovator in zero knowledge on mobile – brought the subject of local encryption control to the fore with the release of iOS 8 in late summer of 2014. Identical complaints (and equally ‘affable’ solutions in exactly the same mould) have emerged in the last 12-14 months from the U.S. attorney general, FBI director James Comey, the UK’s National Crime Agency chief, Barack Obama and David Cameron, and the former Chief of Britain’s Secret Intelligence Service. Not all of them have an equal understanding of the realities of encryption and the consequences of returning the keys to hackable servers, but they all know one thing – they just want it to stop, or at least to go back to the way it was before.
It was predictable that Paris would be a source of emotional capital for this anti-ZK impetus in government, and one has to applaud Vance for waiting a decent interval before exploiting the misery of Parisians; but if the idea of reasonable privacy for the individual was ethically sound before the Paris attacks, it doesn’t cease to be sound even if worse things follow.
Posted by Stu WisePosted : 09:24 AM
post comment
|